
- All
- Tools
- Analytics
- Technical Analysis
- Trading
- Blockchain
- DeFi
- Guides
- Company News
- Educational
- Opinion
- Price Predictions
- Market News
- News
- Trading cases
- Practical guides
- Exchanges
- Trading signals
- Cryptocurrency
- Crypto bots
- Other
Become a crypto master
Learn everything about crypto,
trading and bots

Securing your crypto assets: 2025 best practices
Discover how the landscape of crypto asset security is evolving in 2025, with a focus on mitigating API mismanagement and credential leakage in automated trading. Learn about advanced strategies and software solutions for safeguarding your digital assets.
Start Trading on 3Commas Today
Get full access to all 3Commas trading tools with free trial period

Storing cryptocurrencies safely and securely is an essential part of investing in digital assets. Hackers constantly strive to find new ways to get hold of private keys and steal users’ funds. This article will provide you with everything you need to know about how to safely store digital assets, differentiate between numerous cryptocurrency wallet types, and help you determine the best security options to protect your funds from a range of attacks.
Types of cryptocurrency wallets
One of the obvious implications of the digital nature of cryptocurrencies is the fact that they are stored digitally. Yet, within the digital sphere there are numerous ways to store your digital assets, with each of them providing different levels of privacy and security. Generally, storing cryptocurrencies can be divided into two major categories:
- Custodial – where you trust a third party (such as a centralized exchange or a specialized custodial service) to store your coins
- Non-custodial – where you create your own crypto wallet and take responsibility for securing your digital assets via associated sensitive information (private key/seed phrase)
Non-custodial cryptocurrency wallets store users’ private keys on a local device, and if access to this device or stored information is lost, the user is fully responsible for restoring the funds. In this case, no one can help access the wallet. That’s why when creating a crypto wallet, it is important to pay extra attention to securing private keys and seed phrases which can be used later to recover funds if needed.
Important: never share your seed phrase with anyone. If you are asked for your private key or seed phrase, you are most likely being scammed. The seed phrase is designed to perform a single task: restore access to your crypto assets. If you give up your seed phrase to a third party, they are likely to steal your funds.
There are five major categories of cryptocurrency wallets:
- Hardware
- Desktop
- Mobile
- Browser-based or online wallets
- Paper wallets
Wallets can be further divided into two sub-categories:heavy and light. Heavy cryptocurrency wallets store the full history of their associated blockchain. These types of wallets are called full nodes. They are most often used by miners and die-hard enthusiasts who are adamant about maintaining the highest levels of security. On the flipside, light clients only store associated transactions, and the blockchain data itself is hosted by the wallet provider, so they require the user’s trust.
Note: as a rule, lightweight wallets created for a particular blockchain are safer, because they are designed with the specifics of a particular protocol in mind.
Wallets can also be divided into cold and hot. Cold wallets interact with the blockchain without connecting to the internet, protecting holders’ funds, while hot wallets require a network connection at all times.
Wallets can also be designed to accommodate a specific cryptocurrency like bitcoin, or support multiple currencies — known as multi-currency wallets. Multi-currency wallets can be either single chain or multi-chain. For example, Ethereum wallets are multi-currency but only support Ethereum-based tokens like ERC-20 or ERC-721 token standards. Cryptocurrencies and tokens from other blockchains cannot be stored there.
Best practices to store your seed phrase
A seed phrase — also referred to as a recovery phrase or mnemonic passphrase — is a sequence of 12 or 24 random words that stores information to access a wallet’s private key and serves to gain access to a lost wallet. The backup phrase can be extended with custom passphrases that allow you to create as many hidden wallets as you like and increase the security of your funds, but not all cryptocurrencies support this option. Here are a few tips on how to safely store your seed phrase:
Don’t store the seed on digital devices
Digital devices such as a PC, a laptop, or a smartphone are vulnerable to cyberattacks, especially if you store the backup phrase in an unencrypted form, like a screenshot or text. Hackers can also intercept data from the clipboard when you copy a phrase to save it elsewhere. It is best to keep mnemonics on paper, with a specialized device (more on this later), or any other suitable offline device kept in a hidden and secure place inaccessible to third parties.
Do not share the seed phrase with untrusted parties
You should be the only person with access and knowledge of your seed phrase. The only use for this seed phrase is in case you lose access to your crypto wallet. Anyone asking for your seed phrase likely has malicious intent. If your mnemonic phrase gets compromised, you will likely lose your cryptocurrency: anyone who knows your recovery phrase can get a hold of your crypto assets.
Create multiple copies in different locations
In case you lose or damage one of the copies of your seed phrase, you’ll be able to restore access to your funds by using another copy. It’s also a good idea to store the copies in different locations. That way if one is compromised or destroyed, you can retrieve another copy in a different location. Take some time to explain the recovery procedure to your loved ones so that they can retrieve your funds in case of an unfortunate scenario.
Hardware wallets
In 2023, for those less versed in the intricate world of cryptocurrencies, hardware wallets are often championed as one of the most secure methods for storing crypto assets. (It's worth noting, though, that offline storage of encrypted private keys, when executed correctly, offers a comparable level of security, albeit demanding more technical know-how.) A hardware wallet safely houses your private keys within a fortified chip embedded in a tangible device. Remarkably, even during cryptocurrency transactions, these keys never make contact with the online realm. Instead, coins remain tucked away in cold storage, with the hardware wallet merely authenticating transactions without ever exposing the keys. This ensures that even when interfacing with a potentially compromised system, your hardware wallet's private keys stay out of reach, securely quarantined from any online vulnerabilities.
Here are some of the best hardware wallets for storing cryptocurrencies:
- Trezor T and Trezor Model One – devices that support an additional passphrase. These models are among the few that support open-source secured chips.
- Ledger Nano S and Ledger Nano X – popular wallets with a Secure Element chip.
- Safepal S1 – multi-currency hardware wallets supporting DeFi and staking.
- Cobo Vault Pro and Cobo Vault Essential – also has a mobile cryptocurrency wallet supporting cloud storage of private keys.
- Ellipal Titan – rugged and reliable devices.
- CoolWallet S and Pro – hardware wallets with easy control via a smartphone.
Note: Don’t buy hardware wallets from the vendors not certified by the wallet’s manufacturers as they may have been tampered with, modified, or hacked. Do not use the device if it’s preloaded with a PIN or password. Buy only new and sealed hardware wallets from manufacturers and official re-sellers listed on official websites.
Pros
- One of the safest ways to store cryptocurrencies.
- Cold (offline) storage of private keys.
- Ability to regain access to funds even if the device is lost or fails.
- If hacked, the hacker would need special equipment to access sensitive information.
Cons
- Cost.
- Wear-and-tear over time; can get damaged or lost.
- Less convenient to use – you have to connect the device to your computer each time you need to confirm a transaction.
- The possibility of a physical attack on the Secure Element chip if you lose your wallet (although this risk is quite low).
Desktop wallets
Desktop wallets allow users to store their digital assets in a software-based crypto wallet on a PC or a laptop device. There are both heavy desktop crypto wallets and lightweight ones, with lightweight wallets being more common. Desktop wallets are protected from online threats, such as phishing and browser-based malware, but can be exposed to computer viruses. That said, they are more convenient than hardware wallets since they can be accessed quickly, hence more suitable for everyday use.
Heavy desktop cryptocurrency wallets:
- Bitcoin Core (formerly Bitcoin-QT) is the original decentralized wallet with a full bitcoin node.
- Litecore – desktop full node wallet supporting Litecoin (LTC) storage.
- Geth – a full Ethereum (ETH) node.
- Dogecoin Core – full node wallet for Dogecoin (DOGE) holders.
- Daedalus Wallet – a heavy desktop wallet that allows you to store and stake Cardano (ADA).
Lightweight desktop wallets:
- Electrum – a lightweight bitcoin wallet that supports multisig, two-factor authentication, and SegWit (bech32).
- Wasabi Wallet – an anonymous bitcoin wallet with CoinJoin feature to obfuscate the trail of transactions.
- Exodus – a simple and convenient multi-currency desktop wallet with a friendly interface. There is a mobile version that syncs with the client on the PC.
- Atomic Wallet – multi-currency crypto wallet with strong encryption.
Pros
- More convenient than hardware wallets.
- More secure than online wallets.
- Resistant to online attacks.
- Ability to install a full node on the PC, mitigating trust-related risks.
- Ability to use in conjunction with hardware wallets.
Cons
- Potential exposure to computer viruses.
- Inconvenient to use on the go.
- Full nodes require technical skills and are difficult for beginners to install and use.
Mobile wallets
Crypto wallets for smartphones are convenient to use and allow you to manage crypto assets on the go. Mobile wallets can be protected with a PIN, Touch ID, or Face ID to protect the funds in case the device is lost or stolen.
Note: users can mistakenly download a fake app from the Google Play Store or App Store, so make sure to only download wallets from official developer websites. Never follow advertisement links, as they can lead to phishing attempts that aim to steal users’ funds and confidential information.
Popular mobile cryptocurrency wallets:
- Exodus – a mobile version of one of the most popular desktop wallets. Supports iOS and Android devices.
- Trust Wallet – a secure and convenient multi-currency crypto wallet from Binance with support for several blockchains, such as Ethereum (ERC-20), BinanceBEP (BEP20), and Binance Smart Chain (BSC).
- Electrum – a mobile bitcoin wallet with advanced security features. Only available on Android devices.
- Coinbase – a user-friendly wallet from a well-known cryptocurrency exchange.
- MyCelium – a handy Android wallet to store your bitcoins.
- Trustee Wallet – a simple mobile wallet that allows users to purchase cryptocurrencies and create multiple addresses to store crypto assets.
- Blockchain – a mobile version of the most popular online wallet with support for exchanging, buying, and depositing cryptocurrencies.
Pros
- Convenience.
- Can be used on the go.
- Easy to install and relatively safe.
- Optimal for making regular small payments.
- Storage of many different cryptocurrencies.
- Conveniently transferring coins and tokens with QR codes.
Cons
- Most wallets do not support full nodes.
- Wallets can be compromised if used in public places.
Crypto exchanges
Using cryptocurrency exchanges for the long-term storage of crypto assets is not advised due to their lack of security. One of the key rules of holding crypto is “not your keys – not your coins.” This means, if you don’t control your private key information, you don’t actually control your cryptocurrency. Crypto exchanges hold digital assets for investors and traders who regularly trade cryptocurrencies. But even traders tend to keep most of their funds safely in their wallets for a number of reasons:
- An exchange could go bankrupt or get hacked.
- There’s no guarantee that the exchange won’t freeze your funds under some pretext, such as the illegal origin of the coins.
- Cybercriminals can steal credentials in a variety of ways and hack into a trader’s account.
Note: large exchanges typically keep only a small percentage of their assets on hot wallets. Therefore, even if the exchange is hacked, only a portion of all deposits would be compromised and they can quickly compensate users for the stolen funds.
Pros
- Ability to quickly buy and sell cryptocurrencies.
- Ability to restore access to your funds in case you lost your login/password.
Cons
- Not the best way to store your digital assets for the long term.
- Additional withdrawal fees.
- Security risks and possible withdrawal issues, such as withdrawal limits.
- You do not own your private keys.
Online Wallets
Web wallets are a less secure form of cryptocurrency storage as hackers can steal user credentials and gain access to crypto assets. Still, online wallets are suitable for regular microtransactions due to their ease of use.
Popular web wallets:
Blockchain – one of the earliest popular online wallets in the space.
Green Address – a hot wallet for storing bitcoin. There is a mobile version available for iOS and Android devices.
BitGo – a multisig wallet with advanced security features. It also supports mobile and desktop clients.
MyEtherWallet – a browser-based ETH wallet that supports WalletConnect and hardware device integration. The MEW Connect mobile app is also available.
MetaMask is the most popular plugin for storing ETH and ERC-20 tokens. Recently it added support for Binance Smart Chain.
Pros
- Convenient and fast access to crypto assets.
- Easy to make regular transactions.
- Not tied to a specific device.
- Can quickly create new wallets without having to follow a complex setup procedure.
- Doesn’t take up device memory.
Cons
- Exposure to phishing.
- Not safe to store large amounts of money.
- Doesn’t support full nodes.
Paper wallets
Paper wallets do not require you to download software to manage and store digital assets, so they are not vulnerable to hacking attacks. However, this method of storage has its own issues, as private key information is stored on a piece of paper, which can easily become damaged, lost, or destroyed. If the paper wallet is compromised, your funds will be irrevocably lost. This is why many paper wallet holders laminate their paper wallets in an attempt to keep them from getting damaged. Paper wallets do not generate a seed phrase and contain only the address, public key, and private key, which must be printed out on paper or memorized.
Commonly used paper wallets:
- Bitcoin Paper Wallet – a paper wallet generator for storing bitcoin.
- Bitcoin.com Paper Wallet – a generator from the creators of Bitcoin Cash.
- Wallet Generator – another paper wallet generator for bitcoin wallets.
Pros
- Not susceptible to cyberattacks.
- Cold storage of cryptocurrencies.
- Ability to export a key into any cryptocurrency wallet.
Cons
- Inconvenient for regular usage
- Inability to recover funds in case of loss or severe damage
- Used exclusively for storage.
Comparison of cryptocurrency wallets
Have a look at the table comparing different ways to store crypto assets in terms of convenience and security.
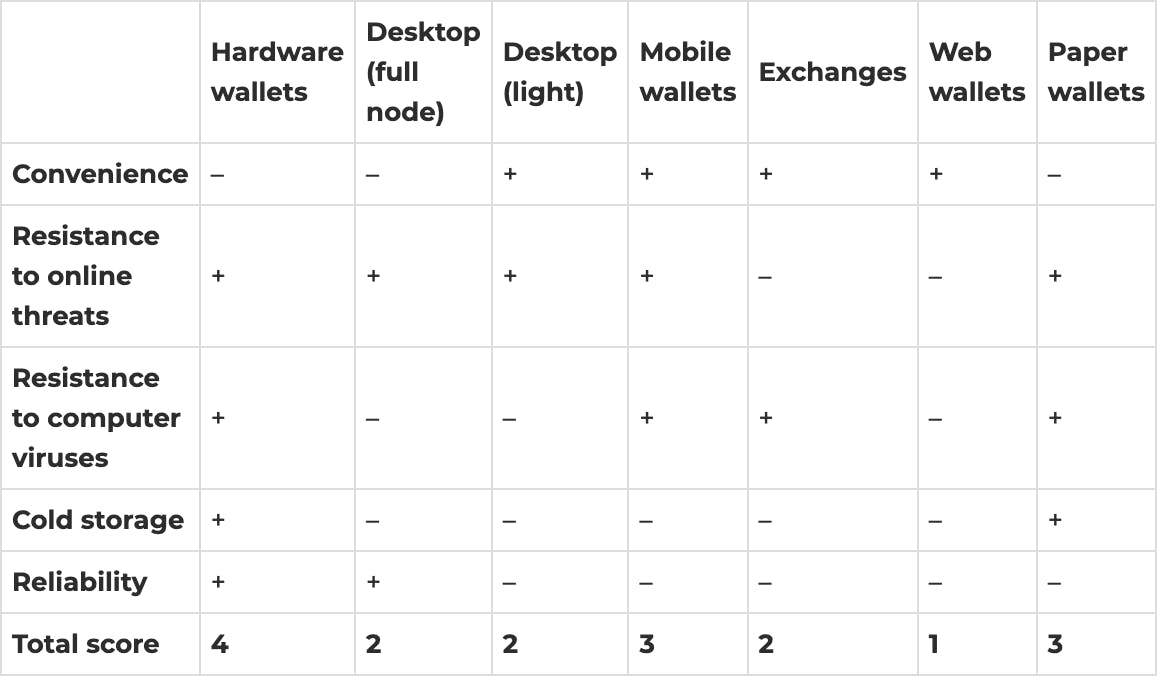
In our comparison, hardware wallets score the best, as they are resistant to malicious attacks and very reliable. In addition, they allow for cold storage of cryptocurrencies. Desktop versions of cryptocurrency wallets can be vulnerable to virus attacks, while web wallets can be vulnerable to phishing attacks. Paper wallets are less reliable because they can be easily damaged, even if laminated.
What is the safest way to store cryptocurrencies?
Using a hardware wallet in combination with a multisignature ( multisig) setup tends to be the most reliable way of storing cryptocurrencies. Even if an intruder manages to steal or hack your device and get a hold of your passphrase or private key, they will not be able to use your assets in any way, because more than one key is necessary to move the funds.
Furthermore, even if you use lightweight mobile or desktop multisig wallets, attackers are unlikely to gain access to all the keys. You can be the owner of all the keys yourself (2-of-3, 3-of-5 or any other setup) or use custodial services, such as Casa’s Keymaster, to store private key information.
Wallets that support multisig:
Which wallet to choose?
There is no single right answer to this question. The choice depends on your goals and the amount of funds you are going to store:
For long-term storage of large sums, it’s ideal to use a hardware wallet with a multisignature setup. This method is inconvenient for everyday use, but it is the most secure approach. If you need a wallet for regular small transactions, then mobile or online wallets are fine – you can use them pretty much anywhere you have an Internet connection. If you store small amounts of money but do not use the wallet very often, it is advisable to use lightweight desktop or mobile wallets.
Conclusion
In 2023, for individuals safeguarding substantial quantities of cryptocurrency, hardware wallets remain the go-to. They seamlessly merge user-friendliness with dependable security.
For those engaged in regular, smaller-scale transactions, streamlined desktop, mobile clients, or web wallets tend to be the most apt.
While paper wallets have begun to feel somewhat antiquated in the crypto storage landscape, they still hold relevance for those seeking extended storage solutions with minimal transaction activity. If you're leaning towards a paper wallet, ensure it's stored in a safety deposit box or another secure environment for optimal protection.
Automation, APIs, and Asset Security in 2025
In 2025, safeguarding digital assets is no longer limited to using hardware wallets or enabling 2FA. As traders increasingly rely on automated crypto trading bots, signal bots, and multi-exchange ai trading bot crypto solutions, the primary threat vector has shifted toward API mismanagement and credential leakage.
Modern crypto bot trading operations often require persistent API connections to enable high-frequency execution, smart order routing, and strategy recalibration. However, with this convenience comes the risk of over-permissioned keys and improper endpoint hygiene. Advanced users now employ automated crypto trading software with key rotation systems, IP whitelisting, and activity-based permission revocation to mitigate exposure.
To meet these demands, software providers like 3Commas offer modular permission settings tailored to each type of bot—be it a grid bot rebalancing stablecoin pairs or an altcoin trading bot scalping volatile assets. These systems allow traders to isolate strategies across exchanges, set withdrawal-disabled keys, and use real-time alerts that monitor bot behavior for anomalies.
Beyond APIs, encryption and secure vault integrations are becoming table stakes for serious traders and asset managers. Institutional participants, in particular, are deploying AI crypto trading bots in secure enclave environments or under MPC (multi-party computation) frameworks to ensure no single party—including the software provider—has full control over transaction execution.
In short, 2025’s security stack is being built not just for wallets, but for bots. The convergence of automated trading and cybersecurity has redefined what “best practices” truly means in a world where bots never sleep and threats never stop evolving.

A proven leader, successful at establishing operational excellence and building high-performance teams with a sharp focus on value creation and customer success.






